Stay Safe Online: Essential Cybersecurity Tips for Everyone
Introduction:
As the economies shift online, security of the same has never been as important as it is today. Cyber threats increase daily in a world where more people buy goods and services, communicate online, and work remotely. infosec is not confined to big organizations; it is an essential requirement for big and small businesses, individuals, and government organizations. This article will discuss the concept of Cybersecurity and its significance to us, the different types of threats we fall victim to, and the measures that can be taken to cover them.
The Importance of Cybersecurity:
Cyber security protects computer hardware, software, communication technical infrastructure, networks, and data against virus attacks, crackers, malicious software, or unauthorized access. This has become essential to our digital lives in driving information’s confidentiality, integrity, and availability. Confidential information can be leaked without significant security policies, organizational networks can be hacked, and the outcome is disastrous.
Types of Cyber Threats:
There are various types of cyber threats that individuals and organizations face today: There are various types of cyber threats that individuals and organizations face today:
Phishing Attacks:
It is a kind of email or message that looks like it is sent from familiar sources to deceive people into passing their private details, such as passwords or credit card information.
Malware:
This consists of computer viruses, worms, and Trojan horses, which intend to destroy or manipulate data, steal information, or penetrate the networks.
Ransomware:
A software that controls and encrypts the user’s information or computer and asks for money to unlock it.
Denial of Service (DoS) Attacks:
These attacks intend to deny a particular machine or a network resource to its intended users by relentlessly sending traffic to the internet site.
Man-in-the-Middle Attacks:
Interception and manipulation of messages between two individuals without their consent is a vector used by the attackers.
SQL Injection:
The code injection type uses a crack in the application’s software to interpose with the queries an application carries out to a database.
Zero-Day Exploits:
These include exploitation of flaws that the creator of the software would rather not have been exposed to in the first place – consequent to which the attacker attains an unfair advantage.
Advanced Persistent Threats (APTs):
Sustained and focused assaults are when an attacker finds his/her way into a network and is not easily discovered by the organization’s security systems.
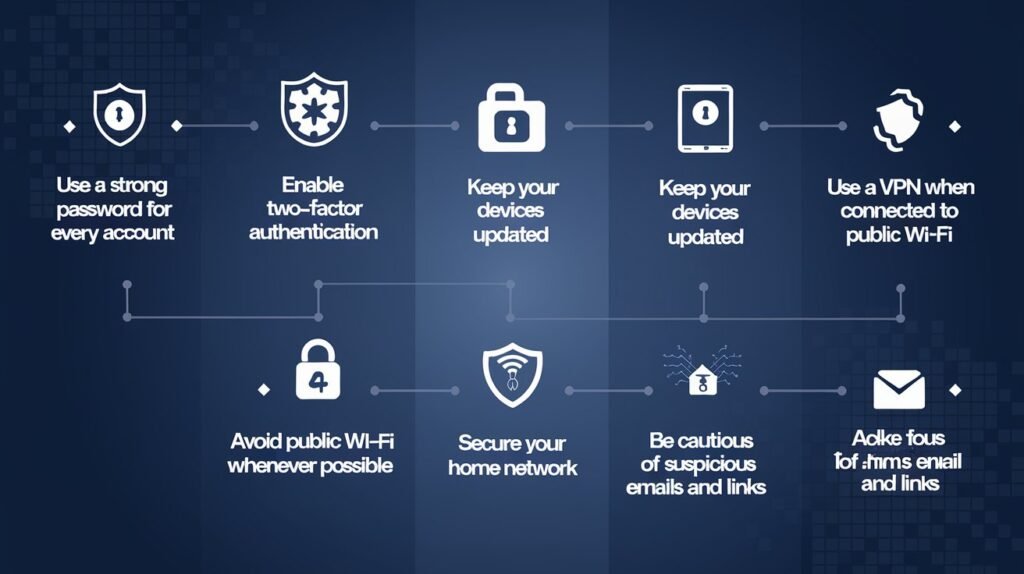
Key Cybersecurity Practices:
Protecting against these threats requires a multi-faceted approach: Protecting against these threats requires a multi-faceted approach:
Strong Passwords:
Always set tough passwords that won’t be easily guessed and also it is advisable to change passwords as often as possible. Do not use the same passwords for different Identities.
Multi-Factor Authentication (MFA):
This makes it even more secure by using two or more verification procedures to log into an account.
Regular Software Updates:
It is necessary always to have updated software, like antivirus and operating systems, to protect against new threats.
Data Encryption:
Secure important data to prevent leakage by unauthorized persons.
Backup Data:
This should enable users to recover their data during a computer virus attack.
Security Awareness Training:
Provide yourself and your employees with the necessary information about the threats that exist at present and how to avoid them.
Firewall Protection:
Employ firewalls to prevent unauthorized access to your network.
Secure Wi-Fi Networks:
A good Wi-Fi password should also be encrypted for the network to avoid people hacking your Wi-Fi.
Cybersecurity has fantastic and terrible consequences for human existence:
On the wonderful side, cybersecurity protects devices and services from malicious assaults orchestrated by hackers, spammers, and cybercriminals. It keeps the structure up to date, prevents facts breaches, and ensures the confidentiality, integrity, and authentication of facts or facts, networks, and gadgets connected to the net.
Advantages of Cybersecurity:
- Data safety from hackers
- Reduces laptop crash
- Decreased records of robbery chance
- System availability and improved information
- Protect commercial enterprise reputation
Cybersecurity enhances our online world security, quickens cyber facts, and improves cyber resilience and statistics protection for agencies and customers. It offers cybercrime, cyber terrorism, botnets, spyware, denial-of-offerings, Man-in-middle assaults, SQL injection, Trojans, malware, and other cyber threats.
Conversely, cybersecurity may be complicated and high-priced and backfire if not implemented correctly.
Disadvantages of Cybersecurity:
- Not low-priced to all people
- Can be complex
- Security patches might also backfire
Cybersecurity measures are difficult to recognize for customers, regular persons, and enterprise men and women as they require much time and effort. If an enterprise doesn’t have a proper security mechanism, it can be easily trapped and attacked by hackers with diverse techniques. Cybersecurity experts need to destroy the complexity of getting via cybersecurity to avoid harm.
In the end, cybersecurity is a blessing to cyber international; despite several benefits, it also has disadvantages. Hackers are also machine professionals who plan assaults for their gain. They may be from other international locations who attempt to fetch personal information about the government, defenses, or people for attacking the u. S . A ..
Realizing the potential of the AI and Machine Learning:
The security role of AI and ML is now at the forefront of maneuvering cybersecurity due to their efficiency in handling large amounts of information. These technologies are used to define trends, estimate possible threats, and even program countermeasures (actions) to threats. For instance, AI can filter through signs pointing towards a breach, while ML will learn how best to respond to the threats as time passes.
The Future of Cybersecurity:
For this reason, as the technologies advance, so will the techniques that the hackers employ. It is suspected that the advancement of artificial intelligence technology will continue to play a vital role in the future of cybersecurity; governments and private sectors will exhibit more dynamics and cooperation, and preventive security measures will be expected. These are the changes one should embrace; hence, it is important to remain abreast and vigilant.
Conclusion:
Cybersecurity is a contemporary and compulsory area of science where new threats appear and changes happen constantly. When it comes down to it, people who are educated on the kinds of threats out there and how to secure themselves against them will not have to endure any significant losses to their digital identities, meaning they will have to get trained. Cybersecurity is important not only for individuals but also for businesses and companies, societies, and governments. Investing in an organization’s security and its employees or customers means investing in a safer future.
FAQs about Cybersecurity:
1. What is cybersecurity?
Cybersecurity involves protecting systems, networks, and data from digital attacks and ensuring the integrity and confidentiality of sensitive information.
2. Why is cybersecurity important?
It is vital for preventing data breaches, identity theft, and financial losses, especially as more aspects of life and business move online.
3. How can I improve my cybersecurity at home?
Use strong passwords, enable 2FA, update your software regularly, and avoid clicking on suspicious links or emails.
4. What are the most common cybersecurity threats?
Phishing, ransomware, malware, and social engineering attacks are some of the most common threats individuals and businesses face.
5. How do businesses protect against cyber threats?
They implement strategies like endpoint protection, encryption, firewalls, and regular employee training to reduce vulnerabilities.
6. What role does AI play in cybersecurity?
AI increasingly detects and responds to cyber threats in real-time, making cybersecurity more proactive and efficient.
TO READ MORE ARTICLES SO CLICK HERE